Introduction:
Modern Web Applications nowadays are relaying on a lot of technologies where typical web applications vulnerabilities are hard to find (eg. Clickjacking is an ABC security bug) but bug hunters are always the best!
Yammer is a freemium enterprise social networking service used for private communication within organizations. Access to a Yammer network is determined by a user’s Internet domain so that only individuals with approved email addresses may join their respective networks.
The service began as an internal communication system for the genealogy website Geni, and was launched as an independent product in 2008. Microsoft later acquired Yammer in 2012 for US$1.2 billion.
.
The bug:
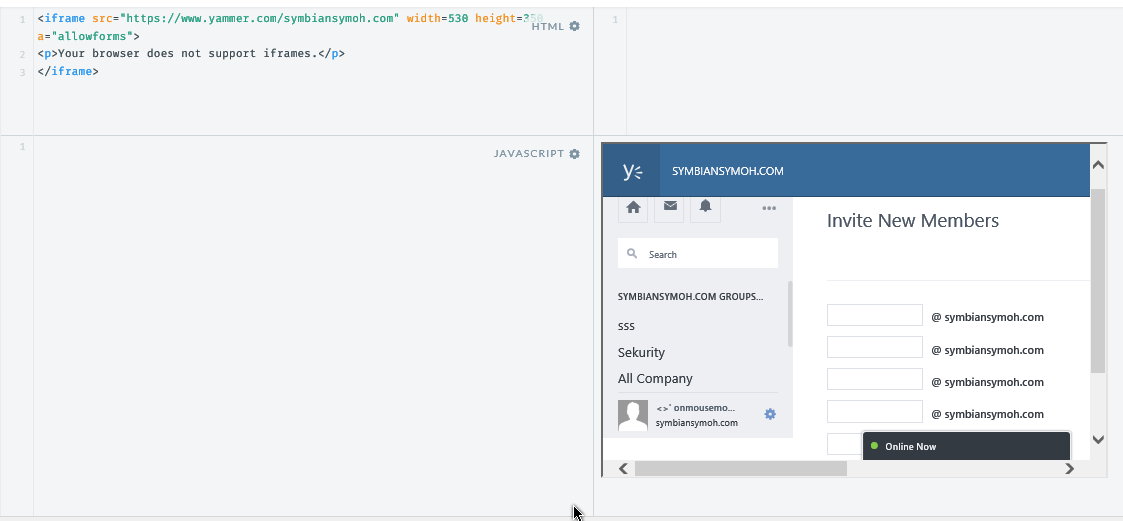
Yammer is not protecting itself from clickjacking with the typical “X-Frame-Options” header but uses a JS frame busting technique to prevent the website to be iframed but by exploiting one of HTML5 Features “Sandboxed Iframes” Iframing Yammer.com will be possible and we will prevent the redirection to the top window location!
.
.
What is Sandboxed iframes?
The sandbox attribute enables an extra set of restrictions for the content in the iframe. When the sandbox attribute is present, and it will:
– Treat the content as being from a unique origin
– Block form submission
– block script execution
– Disable APIs
– Prevent links from targeting other browsing contexts
– Prevent content from using plugins (through <embed>, <object>, <applet>, or other)
– Prevent the content to navigate its top-level browsing context
– Block automatically triggered features (such as automatically playing a video or automatically focusing a form control)
The value of the sandbox attribute can either be just sandbox (then all restrictions are applied), or a space-separated list of pre-defined values that will REMOVE the particular restrictions.
.
Attack Scenario:
Iframing the Settings page or any other sensitive page with a sandboxed iframe to prevent redirecting to top window and allow scripts to be running, fooling the users to do unwanted actions.
.
Impact: What attacker can achieve?
– Change sensitive information of the currently logged in Yammer users (Password, Recovery Emails, etc..)
– Send messages in behalf of currently logged in Yammer users
– Send Contact requests in behalf of currently logged in Yammer users
– Send Group invites in behalf of currently logged in Yammer users
– Etc…
.
PoC Video:
.
The Fix:
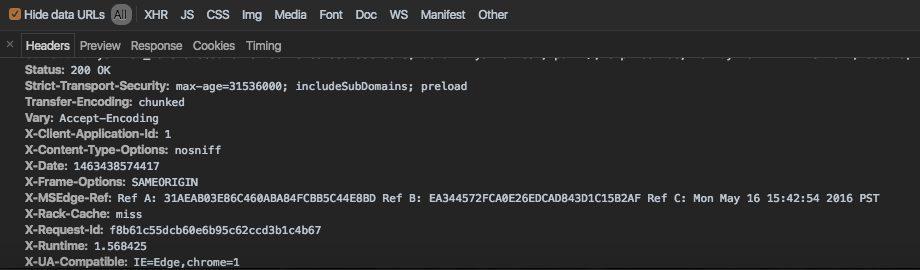
Microsoft fixed the bug affects Yammer social network by applying “X-Frame-Options” header on server side with a value of “SAMEORIGIN” means if you’re lucky and got an XSS it will help a lot (if you couldn’t steal the cookie or reading the anti-csrf value)!
.
Reward:
Microsoft rewarded Seekurity team with a cool undisclosed bounty, Thanks Microsoft!
.
.
Hey!
Building a website? Or already built a one? Think twice before going public and let us protect your business!
ClickJacking Exploiting Features HTML5 Microsoft Security Yammer

Previous Next