What is Asus Control Center?
ASUS Control Center is a whole new centralized IT management software. The software is capable of monitoring and controlling ASUS servers, workstations, and commercial products including notebooks, desktops, All-in-One (AiO) PCs, thin client, and digital signage.

ASUS is focusing on providing convenient, suitable, secured and cost saving solutions for enterprises, small and medium-sized businesses, and data centers across every industry. With the help of ASUS Control Center, your organization is primed to deal with the demands of the most challenging modern IT environments. ~”ASUS CONTROL CENTER WEBSITE”
Long story short:
During our free-time bug hunting (under responsible disclosure rules) we have discovered a misconfiguration issue which led to a critical Information Disclosure vulnerability in their “Asus Control Center” during conducting a passive reconnaissance we have discovered that their Apache Tomcat installation is leaking its configuration file to the public which contains a clear-text database connection password:
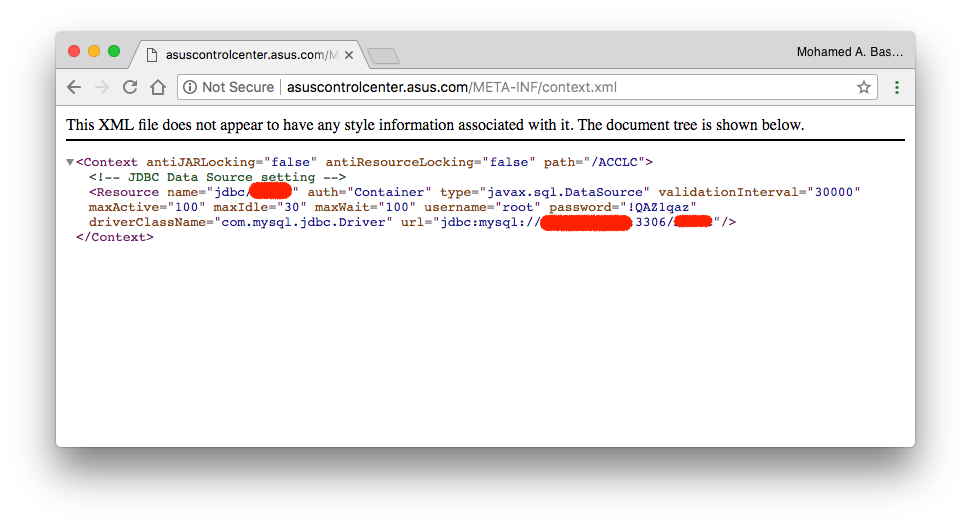
After that we have contacted Asus asking permission for escalation to prove that our PoC is working but they replied us that they acknowledge the issue as it is without any going further so we had to report it as it is.
Then the issue got fixed:
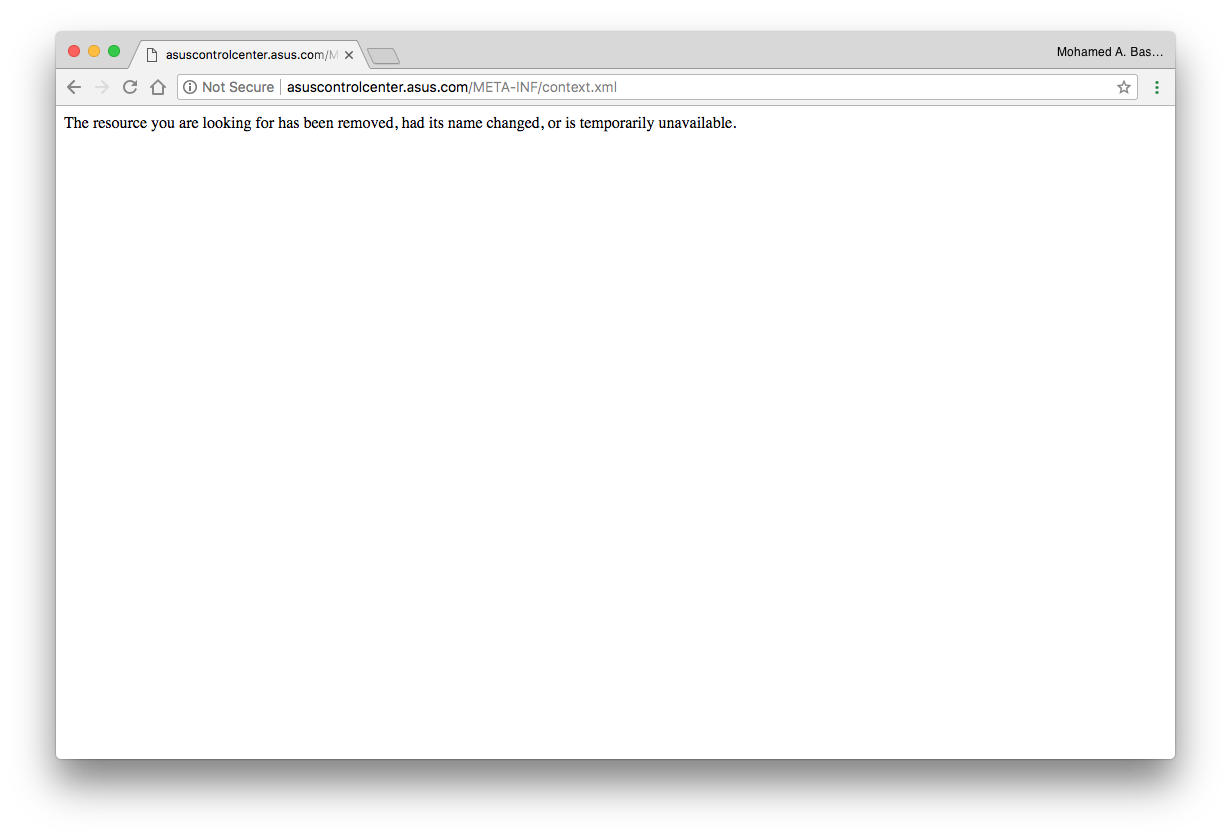
And after that we’ve got an acknowledgment for our submission:
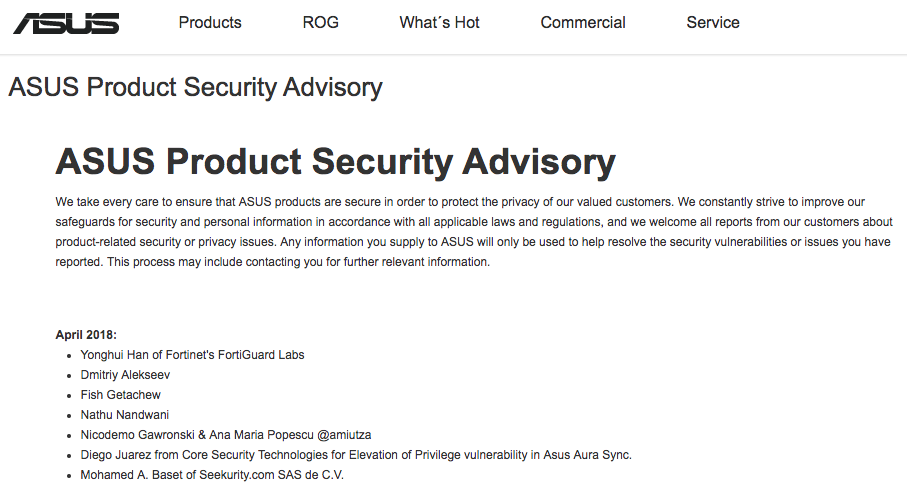
Hall of Fame link: https://www.asus.com/Static_WebPage/ASUS-Product-Security-Advisory/
Vulnerable Product Page: https://asuscontrolcenter.asus.com
Vulnerable Link: http://asuscontrolcenter.asus.com/META-INF/context.xml
.
Time for some conclusion:
- For bug hunters: Do a recon on your target first before anything, Dig into their deep secrets and Brute-force their hidden resources also as a gift use our finding Google dork “inurl:/META-INF/context.xml” and Happy Hunting!
- For server-admins, Developers, Maintaining monkeys: Please take care about your installations and its configurations and be sure that any of sensitive files are exposed to the internet specially if you have “Apache Tomcat” installation aaaand Stay Safe Please!
Thanks for reading!
.
.
.
Hey!
Building a website? Or already built a one? Think twice before going public and let us protect your business!
An and Asus Center Clear-Text connection Control database disclosure Information leakage password Vulnerability

Previous Next