In this blogpost we will clarify how we found A tail of vulnerabilities from leaking thousands of Job Applicants CVs and documents online to Path Disclosure and Information Disclosure Vulnerabilities in one of United Nations WordPress websites but first what is United Nations?
The United Nations (UN) is an intergovernmental organization tasked to promote international co-operation and to create and maintain international order. A replacement for the ineffective League of Nations, the organization was established on 24 October 1945 after World War II with the aim of preventing another such conflict. At its founding, the UN had 51 member states; there are now 193. The headquarters of the UN is in Manhattan, New York City, and is subject to extraterritoriality. Further main offices are situated in Geneva, Nairobi, and Vienna. The organization is financed by assessed and voluntary contributions from its member states. Its objectives include maintaining international peace and security, promoting human rights, fostering social and economic development, protecting the environment, and providing humanitarian aid in cases of famine, natural disaster, and armed conflict. The UN is the largest, most familiar, most internationally represented and most powerful intergovernmental organization in the world. –Wikipedia
WordPress testing methodology:
From the first glance we here at Seekurity when we perform a WordPress testing we first study the nature of the website, is it a medical one? music? media? job application? stores files? is it protecting those stored files? Vulnerable themes? Vulnerable plugins? Misconfiguration issues? Is it using the latest WordPress version? if not, what vulnerabilities hits this specific version? we are trying to profile and cover everything about this website.
We had the time to spend on testing a general target under the responsible disclosure rules which was “United Nations” website, we applied the above mentioned testing methodology and after studying our target we found it a job application website which asks the applicants to upload their CVs to the website through an application interface:
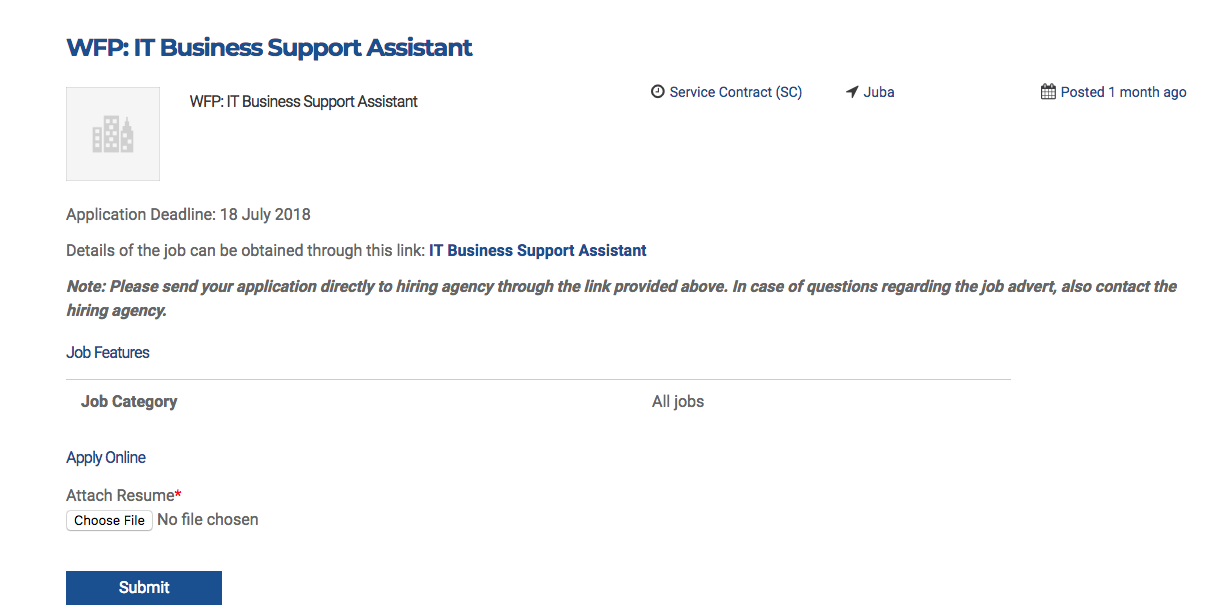
Regardless that the application is not enforcing HSTS which means the application is supporting both HTTP and HTTPS versions, an MITM attacker would get your CV file while uploading it – the application is vulnerable to local path disclosure:
https://ss.one.un.org/wp-includes/rss-functions.php
> Fatal error: Call to undefined function _deprecated_file() in /home/uninsouthsudan/ public_html/wp-includes/ rss-functions.php on line 8
Also leaking thousands of applicants CVs because of a misconfiguration and an open directory listing of the wp-content/uploads folder:
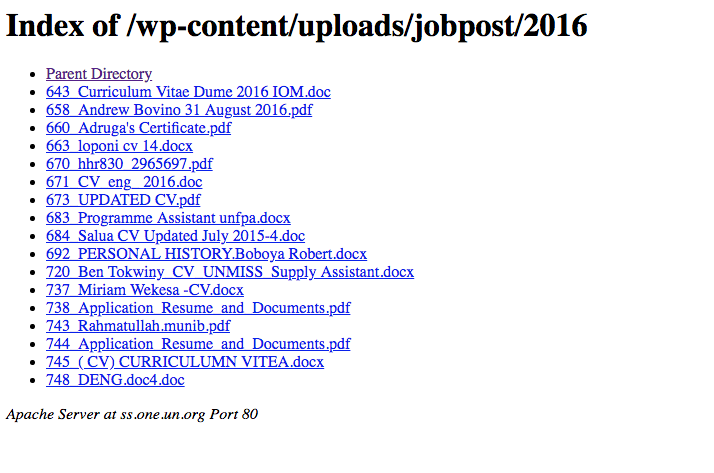
Not to mention the fix for such vulnerabilities is so easy and doesn’t require any massive infrastructure/backend changes.
Proof of Concept Video:
[For owners] If you own a WordPress blog/website here are some advises for you:
- Make sure that your WordPress installation is on the latest update.
- Don’t leave any sensitive files open to public.
- Restrict access to /wp-content/* including uploads/ and others.
- Harden your WordPress installation by using security related plugins.
- Check your installed Themes, Plugins and be sure to have the latest and updated versions of them.
- Don’t keep sensitive files on your server (php.ini, TOP_SECRET.txt, etc…)
- if you’re in Europe and have such vulnerability the GDPR will have you beaten!
[For bug hunters] A little give away:
WordPress local path disclosure: [WordPress-Installation]/wp-includes/rss-functions.php gives you an idea about the installation host username which can help you know more about your target!
Timeline:
- Aug 6th: Initial report has been sent to [email protected].
- Aug 9th: Requesting an initial status about the report, No reply.
- Aug 15th: Requesting another initial status about the report, No reply.
- Aug 27th: We sent a message indicating pushing our full disclosure publicly due to inactivity or no response! “We are pushing our findings publicly due to no response or inactivity!”
- Sep 5th: After struggling to get a reply, someone from UN@Security replied us: “The below reported vulnerability does not pertain to the United Nations Secretariat, and is for UNDP.”
- Sep 24th: No Fix has been pushed after 48 days of the initial report hence Full disclosure occurred.
Disclaimer!
The discovered vulnerabilities have been responsibly reported to the United Nations along with other discovered issues (not mentioned here) including the technical details on how to reproduce the issues, Full disclosure decision has been taken after 48 days of the initial report without fixing.
Update (Sep 26, 2018)
- The Register published an article about our full disclosure of our discovery in the UN website and linked our discovery with some political news which is totally unrelated closely or remotely, Seekurity SAS de C.V. Mexico (THE COMPANY, THE EMPLOYEES, THE CONTENT, THE TECHNICAL DETAILS, THE DISCOVERY OR ANYTHING RELATED) has no close or remote relations or connection of those political news or any non-technical related news.
Thanks for reading, Till the next one!
.
.
.
Hey!
Building a website? Or already built a one? Think twice before going public and let us protect your business!
and Applicants breach CVs disclosure documents Information Information Disclosure Job leak Nations online Path United Vulnerabilities

Previous Next